Flaw allowed bypassing verification code, log in to any Microsoft account
A bug bounty Orion has received $50,000 from Microsoft for characteristic and reporting exposure that would involve faun-forcing the 7-dactyl protection code sent to a drug user to aver identity and access their account.
Independent security measures researcher and white-lid cyberpunk Laxman Muthiyah reportable a vulnerability to Microsoft that could brute-hale the 7-digit security write in code sent to a user's transferrable number or email address to validate identicalness and readjust the password to set out access to the account.
Microsoft has awarded Muthiyah a $50,000 reward under its bug bounty curriculum for coverage the flaw that could allow a threat doer to hijack barely about any Microsoft news report.
Muthiyah is no stranger to characteristic critical bugs. In 2019 he known a badger that could allow anyone to carry out brute-military force attacks for hacking Instagram accounts and was rewarded $30,000.
In 2015 , Muthiyah identified a flaw that could allow him to delete wholly photos from anyone's Facebook account.
The recent flaw is other account takeover scenario, which allows privilege escalation stemming from an authentication bypass used to assert the inscribe sent every bit the account recovery process.
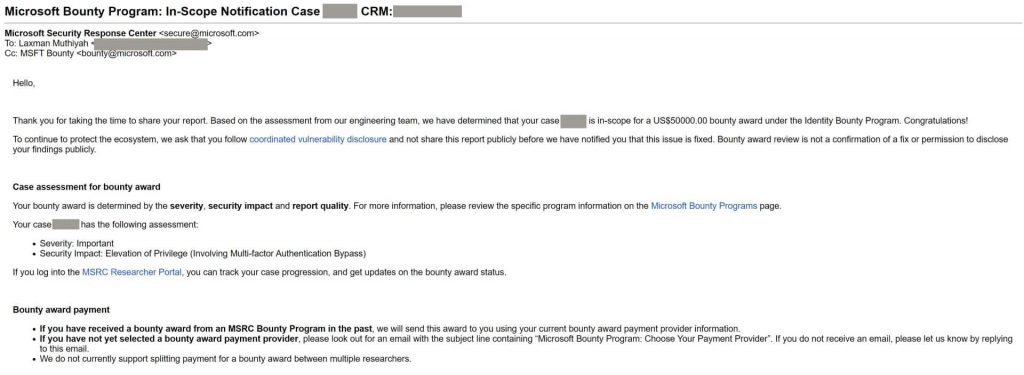
Bug Fixed in 2020
Microsoft fixed the bug in November 2020, untold ahead the details were shared in public by Muthiyah in his web log post published on Tues. His tests showed that out of the 1000 codes sent, just 122 got through, and the others were closed with 1211 error code.
Despite the encoding barriers and plac-limiting checks in place to automatically prevent an attacker from submitting the 10 million code combinations automatically, Muthiyah could crack the encoding operate that disguised the certificate code and sent out multiple co-occurrent requests.
"I complete that they are blacklisting the Information processing plow if all the requests we mail don't hit the host at the same time. A few milliseconds delay between the requests allowed the server to detect the attack and block it," Muthiyah wrote in his blog post.
Attack Works on Accounts Not Secured by 2FA
Muthiyah claims that he could bugger off around the rate-constraining constraint and change the parole to hijack an account, but this attack solitary worked on accounts that weren't secured by two-factor authentication (2FA). However, he also mentioned that it could be extended to licking the two protection layers and qualify the business relationship's watchword.
"Putting all at once, an attacker has to send all the possibilities of 6 and 7 digit security measur codes that would make up around 11 billion request attempts and it has to be sent concurrently to change the password of any Microsoft account (including those with 2FA enabled)."
"IT is non the least bit an light process to send such a massive number of concurrent requests, that would require a lot of computing resources as considerably as 1000s of IP address to complete the attack successfully," Muthiyah terminated.
Did you savour recitation this article? Don River't draw a blank to like our page onFacebook and follow us onTwitter!
Source: https://www.hackread.com/verification-code-bypass-flaw-log-in-microsoft-account/
Posted by: thomastheactiones.blogspot.com


0 Response to "Flaw allowed bypassing verification code, log in to any Microsoft account"
Post a Comment